Zero Trust Security Explained

Unlike traditional cybersecurity models, zero trust security deploys strict identity verification methods for anyone trying to access company resources. It doesn’t matter which device you use or whether you are inside or outside the network; this model trusts no one. Instead, it follows the “never trust, always verify” principle, which improves security and reduces threats.
Our guide thoroughly explains what zero trust security is, how it works, its benefits, and use cases with simple English – no technical terms. It’s the perfect read for beginners.
What Is Zero Trust Security – The Short Version
These are the main points you should know:
- John Kindervag developed zero trust in 2010 when he was an Analyst at Forrester Research.
- The model requests stringent identity verification from anyone trying to access resources.
- Its main technology is Zero Trust Network Access or ZTNA.
- This approach suits modern IT environments with remote access and cloud infrastructure.
- Benefits include a reduced attack surface, minimal damage, and micro-segmentation.
Zero Trust – Definition and How it Works
Businesses have long used traditional security tools like firewalls, antivirus software, and sometimes VPNs to protect valuable systems and data. This model gives anyone inside the network total access to resources while keeping outside threats, well, out. However, the approach is faulty because if attackers infiltrate the network, they can wreak havoc. Hence, a better method was needed.
In 2010, John Kindervag developed a zero trust security model while working as principal analyst at Forrester Research. It aims to provide more effective security to organizations’ most valuable digital assets.
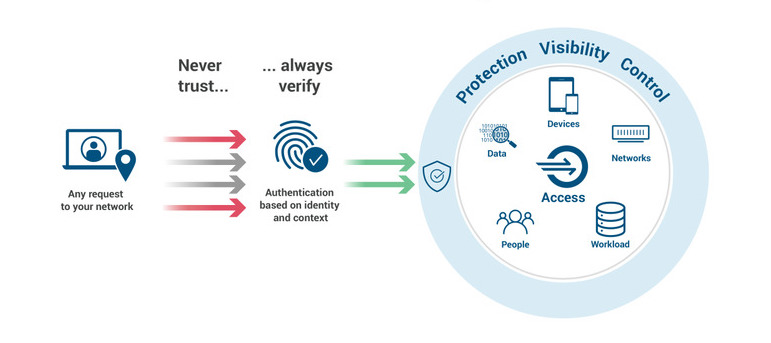
ZT security requests multiple and continuous identity verification from anyone trying to access company resources. It doesn’t matter whether they are inside or outside the network perimeter. Users get access for a limited time and only under the right conditions. In other words, it follows a “trust nothing, verify everything” principle, where systems and data are inaccessible by default.
As a result, businesses can reduce cybersecurity threats and minimize potential damages to limited and isolated areas. And with the switch to remote/hybrid business modules, cloud infrastructure migration, and security transformation, zero trust architecture is becoming increasingly essential.
Much like VPNs, Zero Trust Network Access (ZTNA) allows secure remote access to corporate tools and services. But while VPNs give you full network access, ZTNA enables users to see only the applications they have permission to while the rest remain hidden. And the authentication process occurs through an encrypted tunnel.
Zero Trust Security
Zero Trust Main Principles
By default, zero trust security considers every user, application, or device trying to access the network a potential threat. It only grants access (on a limited basis) once the conditions are met, and the request legitimacy is complete.
The main principles of this module include the following:
- Continuous monitoring and verification: Zero trust verifies identity, permissions, and devices, then grants access on a limited basis. You’ll constantly face connection timeouts, forcing users to re-verify.
- Least privilege access: VPNs give users access to the entire network, whereas ZT security only grants access to a limited part, depending on each user’s permission.
- Multi-factor authentication: Much like the two-factor authentication (2FA) that Facebook, Gmail, and other services apply, this requires more than one proof to authenticate users, not just passwords.
- Microsegmentation: The no-trust module divides security perimeters and breaks them up into small zones. As a result, each section requires different permission, and the surface attack is reduced.
- Device access control: ZT monitors how many devices are trying to access the network, ensures their authenticity, and evaluates them to ensure they aren’t compromised.
- Preventing lateral movement: Threat actors cannot infect the entire network when ZT security is in place. Segmentation quarantines the attacker in one section and prevents them from gaining further access.
Benefits and Use Cases
Zero trust security is ideal for organizations with a remote workforce and cloud infrastructure. But the truth is, any network-relying, data-storing company will benefit from this technology. It narrows attack surfaces, minimizes damages, lowers recovery costs, reduces phishing and identity theft, and eliminates network threats should they creep into the system.
Some of the most common use cases include:
- Upgrading corporate VPNs
- Securing remote connections
- Limiting access to third-party contractors
- Isolating and securing IoT devices
- Segmenting networks
FAQ
What is zero trust security? Here are the answers.
What does zero trust architecture mean?
Contrary to traditional cybersecurity practices, zero trust eliminates implicit trust and continuously validates and verifies every connection. It acts as if any digital interaction is a threat to the system and only grants access under the right circumstances.
What is an example of zero trust?
Zero trust security will help organizations:
- Secure remote connections
- Limit access to third-party contractors
- Isolate and secure IoT devices
- Segment networks
What are the 8 pillars of ZT?
Zero trust requires a wide array of capabilities and securities: Identity, device, network, applications, infrastructure, data, visibility and analytics, and automation and orchestration.
Why is ZT better than a VPN?
VPNs give users access to the entire company network, while zero trust only allows them to see the applications they have permission to. Also, VPNs redirect traffic through multiple servers and then through a central point in the company data center, causing connection speed drops. Meanwhile, ZTNA technology directly connects users to applications without rerouting data through the central point, thus maintaining high internet speed.
Can someone hack zero trust security?
It all depends on how well organizations implement the ZT model. ZT security narrows attack surfaces, minimizes damages, and reduces the impact of identity theft. Worst case scenario, in case there is a breach, companies can isolate the threat and prevent it from spreading to the entire network.
Zero Trust Beginner’s Guide – Conclusion
As companies continue to adopt remote/hybrid work and cloud migration, traditional security methods are not enough to protect against cyber threats. Zero trust security offers a more secure approach by assuming all connections are potential threats and continuously requiring multiple identity verification steps. As a result, the impact will remain minimal even if there is a successful cyberattack.